Introduction
In today’s digitally-driven world, safeguarding your data and network infrastructure is of paramount importance. Whether you’re a small business or a multinational corporation, the threats from cybercriminals, hackers, and malicious software are omnipresent. The need for robust cybersecurity solutions has become more vital than ever before. One of the most essential tools in a business’s cybersecurity arsenal is the firewall. Firewalls act as a barrier between your internal network and the external world, filtering and blocking malicious traffic while permitting legitimate communications to flow freely.
The concept of firewalls has evolved significantly since their inception in the late 1980s, adapting to the changing landscape of network threats. Today, modern firewalls offer a wide range of features designed to secure corporate networks from an array of sophisticated cyberattacks. This article will provide a comprehensive guide on what firewalls are, how they function, and why they are essential for your network security.
1: The Basics of Firewalls
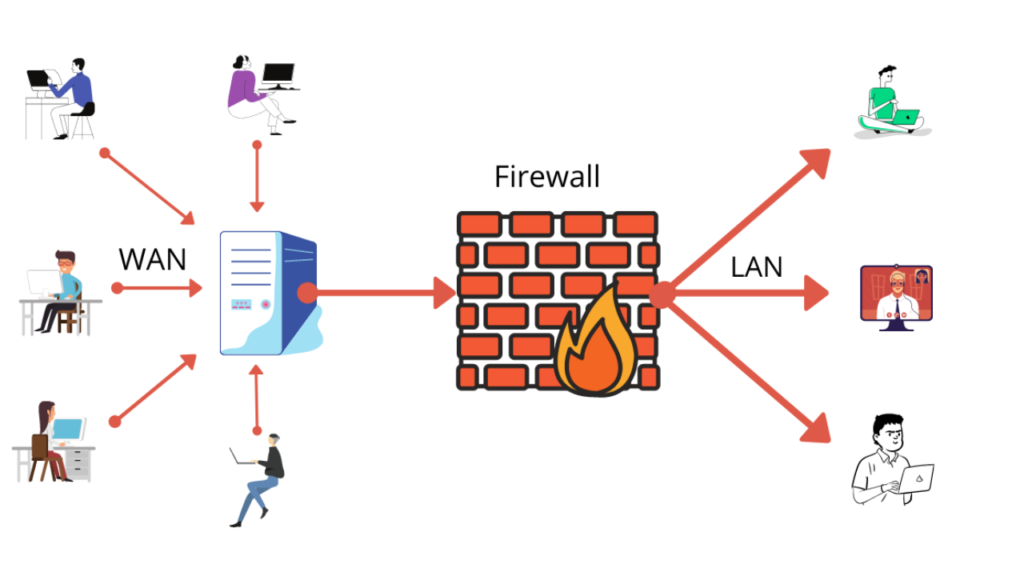
1.1 What is a Firewall?
A firewall is a network security device or software that monitors and controls incoming and outgoing traffic based on predefined security rules. Acting as a gatekeeper between internal networks and external sources, a firewall ensures that unauthorized users, cyberattacks, or harmful data do not infiltrate the network. Firewalls play a pivotal role in protecting networks by filtering traffic and blocking unauthorized access while allowing legitimate data to pass.
The term “firewall” is borrowed from construction, where it refers to a physical barrier intended to prevent the spread of fire between parts of a building. In a similar manner, firewalls in networking isolate the trusted, internal network from untrusted external networks, such as the Internet.
1.2 How Firewalls Work
At its core, a firewall inspects data packets the small units of data transmitted across a network. These data packets contain information such as the source address, destination address, and the content of the data itself. Based on predefined rules or policies, the firewall analyzes whether a packet should be allowed or blocked.
Firewalls can work at various levels of the OSI model (Open Systems Interconnection), which defines the communication functions of a network. For example, a basic firewall may work at the network layer, controlling traffic based on IP addresses and protocols. More advanced firewalls operate at the application layer, inspecting the actual content of traffic to detect suspicious behavior.
1.3 The Importance of Firewalls
As digital technologies continue to evolve, so do the methods cybercriminals use to breach networks. This is why firewalls have become an integral part of a comprehensive cybersecurity strategy. Without a firewall, any network would be exposed to potential security breaches, leaving valuable data vulnerable to theft or damage.
Here are some key reasons why firewalls are critical for network security:
- Protection Against Unwanted Traffic: Firewalls filter traffic entering or exiting the network, ensuring only authorized data packets gain access.
- Prevention of Unauthorized Remote Access: Firewalls can be configured to block access from malicious external sources attempting to enter your network.
- Enhanced Privacy: By blocking malicious traffic, firewalls ensure sensitive data remains private and secure from cybercriminals.
2: Types of Firewalls

There are various types of firewalls, each with its own set of features and use cases. Understanding the different types of firewalls is crucial to implementing the right solution for your business.
2.1 Packet Filtering Firewalls
One of the simplest forms of firewalls, packet filtering firewalls, work by analyzing individual data packets. They inspect packets based on parameters such as IP addresses, port numbers, and protocols. If the packet matches the firewall’s predefined rules, it is allowed through; if not, it is blocked.
Packet filtering firewalls are usually implemented at the network layer of the OSI model and are known for their speed and simplicity. However, they are limited in their ability to inspect the actual content of the data, making them less effective against sophisticated threats.
2.2 Stateful Inspection Firewalls
Stateful inspection firewalls are an advancement over packet filtering firewalls. While packet filtering focuses solely on individual packets, stateful firewalls maintain records of active connections. By keeping track of the state of connections, stateful firewalls can make more informed decisions about whether to allow or block traffic.
Stateful firewalls work by monitoring the full context of network traffic. They analyze packets not just based on individual attributes but also in relation to the state of the ongoing connection. This makes stateful firewalls more secure than packet filtering systems.
2.3 Proxy Firewalls
Proxy firewalls, also known as application-level gateways, operate at the application layer of the OSI model. Instead of directly passing data between the internal and external network, a proxy firewall intercepts traffic, makes security decisions, and forwards it on behalf of the client. This isolation ensures that the internal network remains protected.
Proxy firewalls offer the benefit of inspecting the actual data within the packets, enabling more granular control over what is allowed through. They are often used in environments that require a higher level of security, though they may introduce more latency than other types of firewalls.
2.4 Next-Generation Firewalls (NGFWs)
Next-generation firewalls (NGFWs) are an evolution of traditional firewalls, designed to offer deeper inspection of traffic. NGFWs incorporate features such as deep packet inspection (DPI), intrusion prevention systems (IPS), and application awareness. Unlike traditional firewalls that focus primarily on ports, protocols, and IP addresses, NGFWs can analyze traffic at the application layer, identifying and controlling specific applications.
In addition to identifying applications, NGFWs can detect advanced threats, malware, and even encrypted traffic, making them a powerful tool in the fight against cyberattacks.
2.5 Unified Threat Management (UTM) Firewalls
Unified threat management (UTM) firewalls offer a comprehensive solution by combining multiple security features into a single appliance. These firewalls typically include traditional firewall capabilities along with antivirus, antimalware, VPN, and intrusion prevention systems (IPS). UTM firewalls are often favored by small to medium-sized businesses (SMBs) that need an all-in-one security solution.
While UTM firewalls provide a broad range of security functions, they may not be as customizable or scalable as specialized solutions for larger enterprises.
3: Firewall Deployment: Where and How?
Proper deployment of a firewall is crucial to ensuring the best protection for your network. Firewalls can be deployed in various ways, depending on the size and architecture of the network, the specific security needs, and the complexity of the threats faced.
3.1 Perimeter Firewalls
Perimeter firewalls are placed at the boundary between an internal network and the external Internet. Acting as the first line of defense, perimeter firewalls are responsible for filtering incoming and outgoing traffic. They serve as the most basic layer of protection against cyber threats.
Deploying perimeter firewalls is essential for any organization with external connectivity. They are typically used to filter traffic based on IP addresses, protocols, and ports, ensuring only legitimate requests reach the internal network.
3.2 Internal Firewalls
Internal firewalls are used to segment internal networks, restricting communication between different segments. This is particularly useful in large enterprises, where internal firewalls can prevent the spread of malware or unauthorized access between departments. For example, a company may implement internal firewalls to separate the HR department’s network from the finance department’s network, ensuring sensitive data remains secure.
Internal firewalls are also a key component in zero-trust architecture, a security model that assumes no part of a network can be trusted by default.
3.3 Cloud-Based Firewalls
With the rise of cloud computing, organizations have increasingly turned to cloud-based firewalls, also known as firewall as a service (FWaaS). These firewalls are hosted in the cloud, providing flexible, scalable security for businesses that operate in cloud environments.
Cloud-based firewalls are ideal for organizations that rely on cloud platforms such as Amazon Web Services (AWS), Microsoft Azure, or Google Cloud. By protecting cloud infrastructure, these firewalls ensure that data stored in and accessed from the cloud remains secure.
3.4 Hybrid Firewalls
A hybrid firewall combines both on-premise and cloud-based firewalls to create a cohesive security solution for organizations with both physical and cloud infrastructure. Hybrid firewalls offer the best of both worlds, allowing businesses to secure traditional data centers while simultaneously protecting their cloud environments.
Conclusion
As you can see, firewalls are an essential tool for protecting your network from the ever-evolving threat landscape. From small businesses to large enterprises, the right firewall solution can safeguard valuable data, prevent unauthorized access, and maintain network integrity.
KnoTra Global Firewall Solutions
At KnoTra Global, we specialize in providing tailored firewall solutions to protect your network from emerging cyber threats. Our services include:
- Firewall Installation & Configuration: We help businesses deploy and configure firewalls suited to their specific needs.
- Managed Firewall Services: We offer comprehensive firewall management, monitoring, and support to ensure continuous protection.
- 24/7 Monitoring and Support: Our expert team provides real-time monitoring and threat detection to keep your network safe.
For more information, visit KnoTra Global Firewall Solutions.

As the IT & Marketing Director at KnoTra Global, Ravi leverages over 16 years of expertise in IT, digital marketing and business consulting to enhance the client company’s strategic initiatives. His role is pivotal in integrating advanced marketing strategies with KnoTra Global’s extensive IT services, enriching our cybersecurity, cloud solutions, and IT support. Ravi’s innovative leadership ensures that KnoTra Global remains at the technological forefront, empowering our clients with robust tools and strategies for sustainable growth and success. His approach drives the company’s vision forward and sets a benchmark in delivering client-centric IT solutions.

